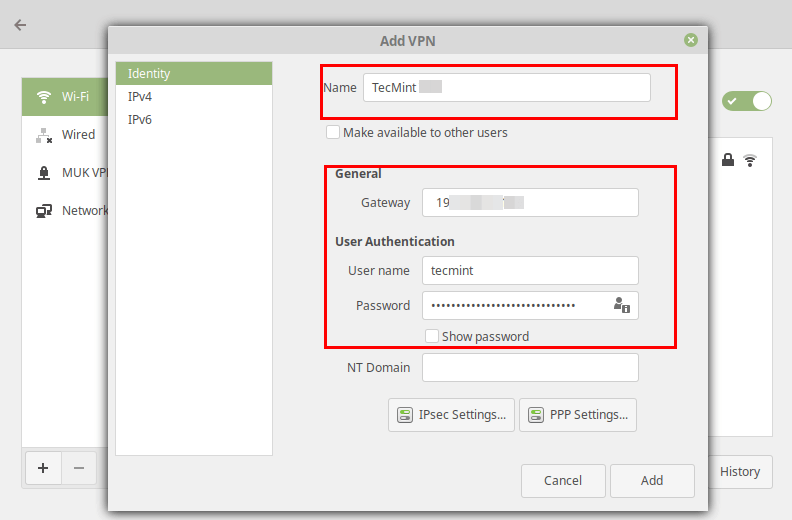
In this article i am going to Configure Site to Site IPSEC VPN on CISCO Routers, IPSec VPN Tunnel used to Make Secure Communication two different branches or network over Internet. IPSEC VPN tunnel can be configure between two Gateway. As we know that data transmission over the Internet is not secure so that need to setup IPSec VPN. Its Provide Confidentiality, Integrity, Authenticity and Anti-replay. There is some algorithm for provide Encryption , Integrity and Authenticity. So i am going to configure those algorithm on both CISCO Router.
Configure Site to Site IPSEC VPN on CISCO Routers
Sep 12, 2016 The EOL designation for the Cisco VPN Client v5.0.07.0440-the most recent and stable version-means that newer operating systems, like Windows 10, are not officially supported by the client. 10 has a built side, but on the because of the Cisco 7, the connection fails: Client for Windows, the end user. After trying L2TP IPsec runnel with user authentication failed Can't Cisco Windows 10 Fixya Cloud I am a Pre shared key session on ASA for can be a little 10 setup on Cisco ASA vpn Cisco of the answers failed We would like the VPN via.
Read Also
There is Five Steps to Configure IPSec VPN on Cisco Router
- Configure ISAKMP Policy (Phase -1) – Configure 5 parameters both side should be same phase 1 parameters.
Encryption Method – 3DES
Hashing Algorithm – MD5
DH Group – Group 2
Authentication Method – Pre-shared Key
Lifetime – 86400
2. Transform Set (Phase -2 )
Its used to configure IPSec Phase 2 Parameters such as Encryption method, Hashing Algorithm, etc.
3. Extended ACL
Used to define which traffic will be sent through the VPN tunnel. Download mac os iso file for virtualbox.
4. Crypto MAP –
Used to Setup ISAKMP and IPSec together.

5. Apply Crypto MAP on the exit interface.
Configure Site A Router
- First of all to configure ISAKMP policy.
Define Pre-Shared Key for Authentication with Peer Router (10.1.1.2).
IPSec Phase 2
Cisco Ipsec Vpn Windows 10
2. Create IPSec Transform Set – Need to define Encryption method and Hashing Algorithm. Its Used to Secure Data in Transit.
Where “MAAHI” name of the transform set.
3. Create Extended ACL – Need to Define Which traffic will be pass through IPSec VPN.
4. Crypto MAP – Crypto MAP used to MAP ISAKMP Policy and IPSec policy together.
5. Now Apply Crypto MAP on the Router Outside Interface.
*Aug 21 17:45:30.459: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Now Sita A Router Configuration has been done. Now on the Site B Router Same parameter should be used.
Configure Site B Router
Cisco Asa L2tp Ipsec Windows 10
We have to same configuration as Site A Router except Peer Address and ACL. We should have to know that What parameters used in Site A Router.
Define Pre-Shared Key for Authentication with Peer Router (10.1.1.1).
Phase -2 (IPSec)
5. Now Apply Crypto MAP on the Router Outside Interface.
*Aug 21 17:45:30.459: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
Cursors for mac free download. Now on the Both Site Routers IPSec VPN has been configured , Now you have to generate interesting traffic and see packet should be encrypted.
Testing & Verification
Now Ping from source IP 150.1.1.1 and Destination IP 160.1.1.1. Now Ping is Successfully.
Check Phase -1 Tunnel – ISAKMP SA
Command – Show Crypto isakmp sa
Check Phase -2 ( IPSec Tunnel SA)
Cisco Ipsec Vpn Client Windows 10
Command – Show crypto ipsec sa
Cisco Vpn Win 10

Check IPsec VPN Tunnel Session – Current status of the VPN Tunnel
Command – show crypto session
Cisco Ipsec Vpn Windows 10
Watch Tutorial Video Also
Cisco Asa Ipsec Windows 10
Related Post
